The NPM ecosystem just got hit with its most sophisticated supply chain attack to date, and it’s not even subtle about its intentions. Dubbed “Sha1-Hulud” (a cheeky nod to the giant Dune sandworms), this malware campaign has turned 1,000+ packages, including critical infrastructure from Zapier, ENS Domains, PostHog, and AsyncAPI, into unwitting data exfiltration agents. The attack isn’t just stealing credentials, it’s weaponizing the entire JavaScript development lifecycle against developers.
The Anatomy of a Supply Chain Worm
The attack’s brilliance lies in its simplicity. Attackers compromised legitimate packages by adding a malicious preinstall hook that executes before installation even completes. The payload structure reveals a multi-stage operation:
{
"name": "@asyncapi/specs",
"version": "6.8.2",
"scripts": {
"preinstall": "node setup_bun.js"
}
}
The innocent-looking setup_bun.js script downloads or locates the Bun runtime, then executes the heavily obfuscated bun_environment.js, a 10MB payload designed to evade casual inspection.
Once activated, the malware establishes two primary workflows:
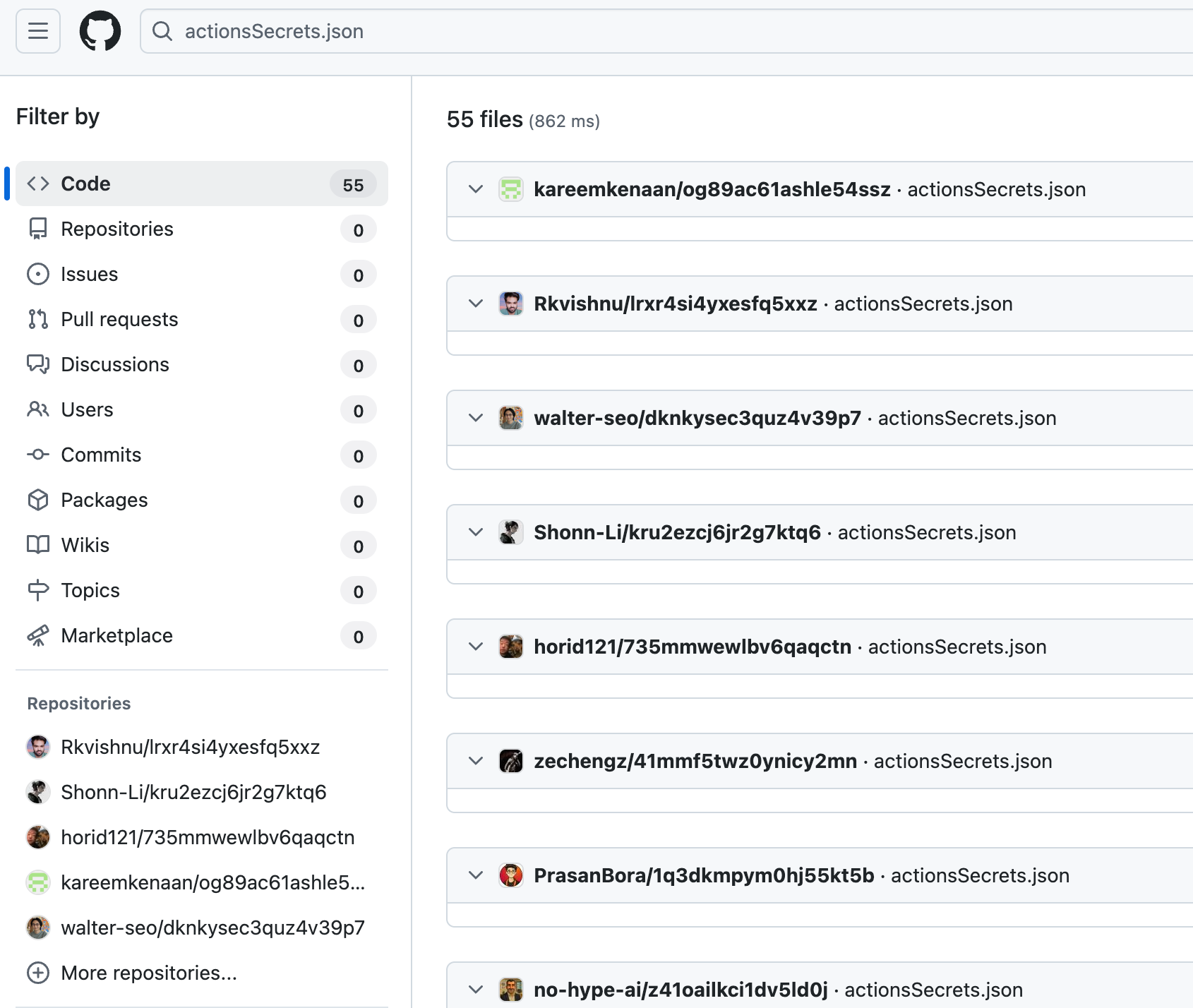
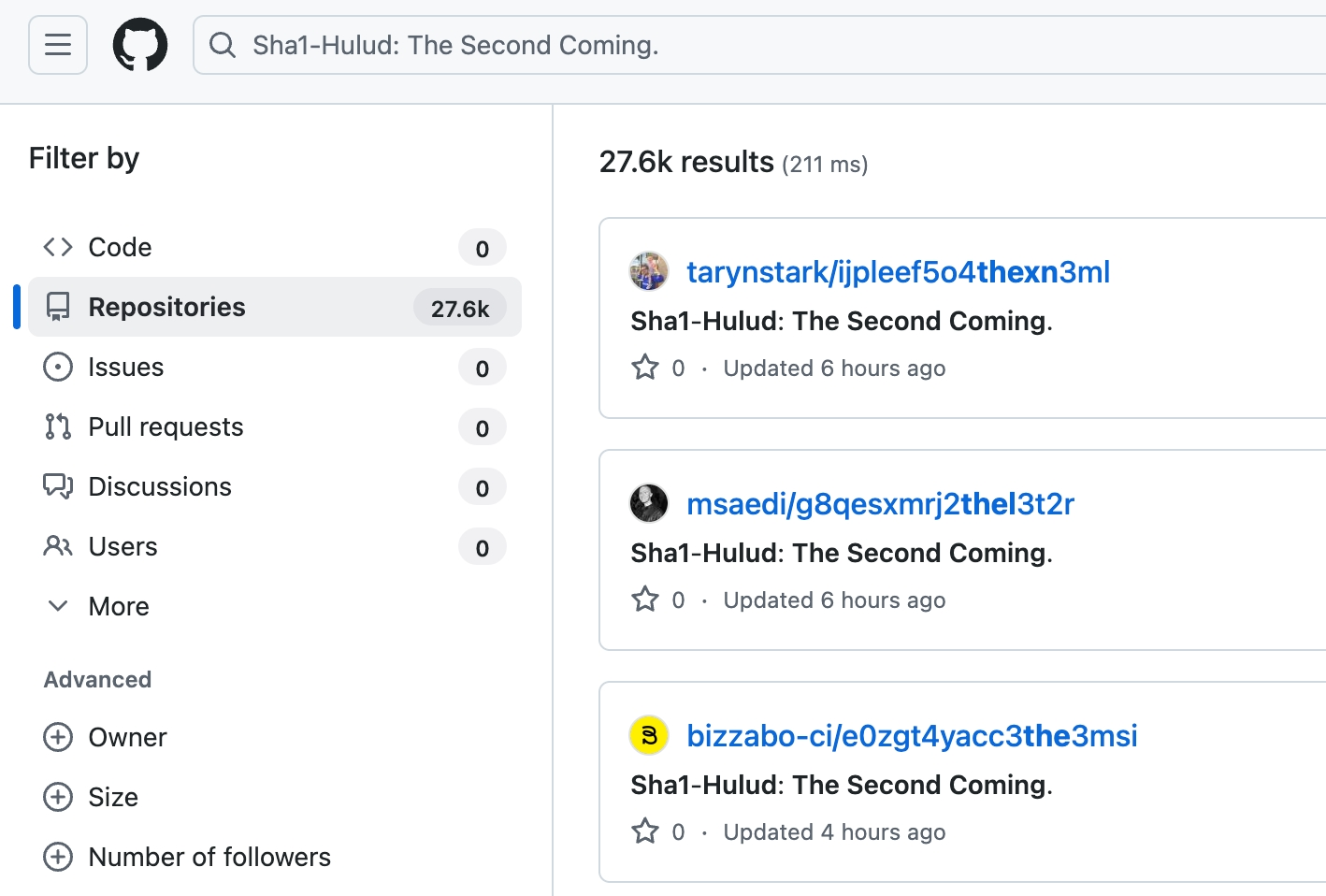
Credential Harvesting: It scans for NPM tokens, AWS/GCP/Azure credentials, and GitHub tokens using TruffleHog, then exfiltrates them to attacker-controlled GitHub repositories named with the telltale description “Sha1-Hulud: The Second Coming.”
Self-Replication: Using stolen NPM tokens, the malware automatically infects other packages maintained by the victim, incrementing version numbers and republishing them with the malicious payload included.
Cross-Victim Infection and Data Destruction
What makes this attack particularly insidious is its network effect. Wiz Research confirmed that cross-victim exfiltration is occurring, where one victim’s secrets get uploaded to repositories owned by other compromised developers. This creates a resilient botnet-like network where compromised systems inadvertently aid the attacker’s operation.
But the real kicker? This malware contains a “dead man’s switch” that GitLab researchers identified. If infected systems lose access to both GitHub (for exfiltration) and NPM (for propagation), the malware triggers immediate data destruction:
- Windows systems: Attempts to delete all user files and overwrite disk sectors
- Unix systems: Uses
shredto overwrite files before deletion
The implications are terrifying, coordinated takedown attempts could trigger mass data destruction across thousands of developer machines.
The Scale is Unprecedented
According to Wiz Research, over 25,000 repositories have been created across approximately 350 unique GitHub users, with new repositories appearing at a rate of about 1,000 every 30 minutes at the attack’s peak. The preliminary impact assessment reveals staggering numbers:
- 775 compromised GitHub access tokens
- 373 AWS credentials
- 300 GCP credentials
- 115 Azure credentials
The attack’s timing is particularly cynical, coming just before NPM’s December 9 deadline to revoke classic tokens, attackers squeezed in one last major supply chain hit before authentication methods hardened.
Why This Attack Succeeded
The success of Shai-Hulud reveals fundamental weaknesses in our software supply chain:
Trust Transitivity: Developers implicitly trust packages from established organizations like Zapier, ENS Domains, and PostHog. When those packages get compromised, the blast radius becomes enormous.
Lifecycle Script Blind Spots: Most security tools focus on runtime execution, but preinstall scripts run during package installation, often in privileged CI/CD environments with access to secrets.
Credential Sprawl: The malware successfully harvests credentials because they’re scattered across environment variables, config files, and development environments.
Package Manager Trust Model: NPM’s trust model assumes maintainer accounts are secure, but offers limited protection when those accounts are compromised.
The Attack’s Evolutionary Improvements
This isn’t the first Shai-Hulud campaign, but it’s significantly more sophisticated than its September predecessor. Key improvements include:
- Bun Runtime Integration: Using Bun as an execution environment ensures the malware runs even in environments without Node.js installed
- Enhanced Propagation: Infects up to 100 packages per compromised account (versus 20 in the previous attack)
- Random Repository Names: Creates randomly named repositories rather than hardcoded ones, making detection more difficult
- Self-Healing Network: Cross-victim token sharing creates redundancy in the malware’s infrastructure
Immediate Actions for Security Teams
If your organization uses NPM packages, here’s your checklist:
Credential Rotation: Assume compromise and rotate ALL credentials, NPM tokens, GitHub PATs, cloud credentials, SSH keys. Everything.
Package Audit: Check dependencies against the impacted packages list and remove compromised versions immediately.
npm cache clean --force
rm -rf node_modules
GitHub Investigation: Search for repositories with “Sha1-Hulud: The Second Coming.” in their description and review .github/workflows/ for suspicious files like shai-hulud-workflow.yml.
Pipeline Hardening: Disable lifecycle scripts in CI/CD where possible and implement network restrictions for build systems.
The Bigger Problem: Supply Chain Trust is Broken
The Shai-Hulud attacks highlight that our current software supply chain security model isn’t just inadequate, it’s fundamentally broken. We’ve built an ecosystem where a single compromised maintainer account can poison hundreds of packages affecting millions of downloads, yet our detection and response capabilities remain reactive at best.
The attack leverages the very automation that makes modern development efficient against itself. CI/CD pipelines with broad permissions become unwitting malware distribution networks. Development machines with access to production credentials become data exfiltration endpoints.
What’s particularly alarming is how the malware exploits legitimate tools, using GitHub Actions for persistence, TruffleHog for credential scanning, and Docker for privilege escalation. The boundaries between legitimate automation and malicious activity have never been blurrier.
Moving Beyond Reactive Security
The Shai-Hulud campaign demonstrates that traditional vulnerability scanning isn’t enough. Organizations need:
- Behavioral monitoring for package installation processes
- Credential isolation that separates build-time secrets from runtime execution
- Package signing and verification mechanisms
- Zero-trust approaches to dependency management
This attack should serve as a wake-up call: our software supply chain has become a critical infrastructure component, and it’s being actively weaponized. The question isn’t whether there will be more attacks like Shai-Hulud, but when, and whether we’ll be prepared for the next evolution.
The sandworm has breached the shield wall. Now we need to figure out how to survive in the desert.